Blog
How Much Does Security Awareness Training Cost?
Discover the true cost of cyber threats in 2023. With data breaches hitting an average of £4.45 million, safeguard your business with security awareness training. Find out why investing is vital.
Does Security Awareness Training Work?
Elevate security awareness training by customising content, adding interactivity, and staying current with threats. Measure progress and promote a culture of security to fortify your organisation's defences.
How Often Should Security Awareness Training be Conducted?
In the face of increasingly sophisticated cyber threats, organisations must invest in employee security awareness training. But how often should this training occur for maximum effectiveness?
5 Steps to Foster an Effective Information Security Culture
Enhance your organisation's security posture with 5 essential steps to foster an Information Security Culture. Equip your workforce with knowledge and tools through awareness training, interactive learning, and customisation.
Calculating the ROI of Security Awareness Training
Discover the financial benefits of Security Awareness Training. Mitigate evolving cyber threats and safeguard your organisation. Learn to calculate ROI and explore the many advantages, from reduced incidents to potential insurance savings. Make informed decisions to protect your sensitive information and assets.
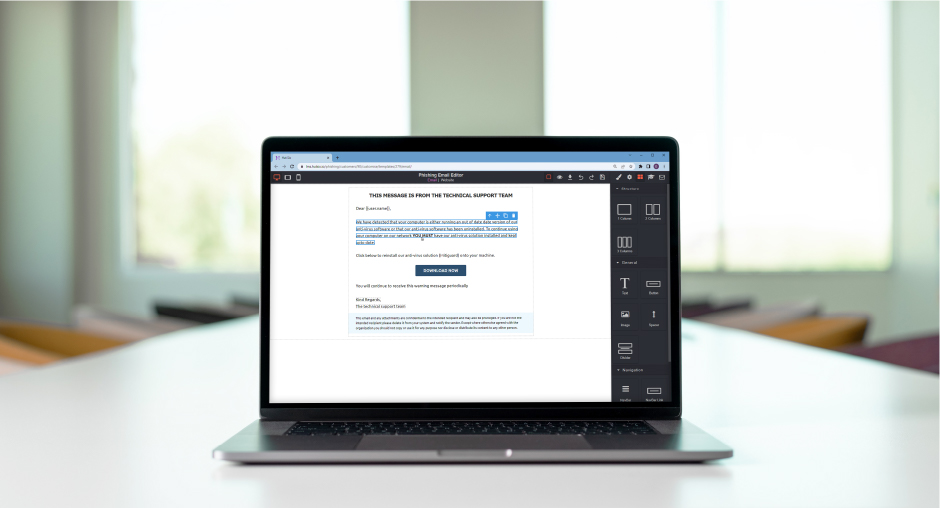
Introducing Hut Six's New Phishing Simulation Editor - Hut Six
Enhance Employee Security Awareness with Hut Six's Phishing Simulation Editor. Craft, customise, and deploy realistic phishing attacks effortlessly. Choose from 50+ pre-designed templates or build your own. Test, train, and educate with ease.
What is the Impact of Security Awareness Training? - Hut Six
Discover the Impact of Security Awareness Training: Prevent breaches, foster culture, & build trust.
Measuring the Effectiveness of Security Awareness Training
Discover the key metrics to evaluate the effectiveness of security awareness training. Learn how employee feedback, compliance metrics, completion rates, ROI calculations, and continuous evaluation can optimise your training program.
What is the difference between SOC 2 type 1 and type 2? - Hut Six
Discover the differences between SOC 2 Type I and Type II reports. Learn why a Type II report can demonstrate ongoing effectiveness, meet customer requirements, ensure compliance, enhance trust, and promote continuous improvement.
LinkedIn Crypto Scam: Celebrity Endorsements
LinkedIn Crypto Scam: Beware of Celebrity Endorsements and Stay Safe Online - Learn the essential steps to protect yourself from crypto scams and online fraud. Be vigilant, verify information, and avoid unsolicited offers. Educate yourself and adopt secure practices to minimise the risk of becoming a victim. Get informed with our free bite-sized awareness training.
What is Personal Data?
Learn about personal data, its types, and significance in data protection. Explore general and special category data, as well as pseudonymised and anonymised data under the GDPR.
A Guide to Types of Sensitive Information - Hut Six
Discover the types of sensitive information that require special handling and protection. Learn about personally identifiable information (PII), trade secrets, intellectual property, financial data, medical records, legal case details, and classified government documents.
ISO 27001 Certification Process
Obtain a comprehensive step-by-step guide to achieve ISO 27001 certification for your business. Understand the benefits of ISO 27001, such as enhanced information security, stakeholder confidence, regulatory compliance, and continual improvement.
Cyber Essentials Checklist
Discover the essential checklist for Cyber Essentials certification, including requirements and steps to meet. Learn how to evaluate, implement, and document cybersecurity measures to obtain certification and comply with industry standards.
What is Data Destruction
Discover the importance of data destruction and why it's crucial in today's digital age. Learn how to protect yourself and your business from data breaches and ensure the safe and responsible handling of confidential data.