Introducing Hut Six's New Phishing Simulation Editor
Hut Six is proud to announce the release of our brand-new, state-of-the-art, phishing simulation editor. Packed with features to make customising your simulated phishing attacks simple and painless, testing employee anti-phishing skills has never been easier.
With over 50 pre-designed phishing email templates to choose from (as well as many more on the way), you can pick the right emails to train your employees to identify, avoid and report suspicious emails.
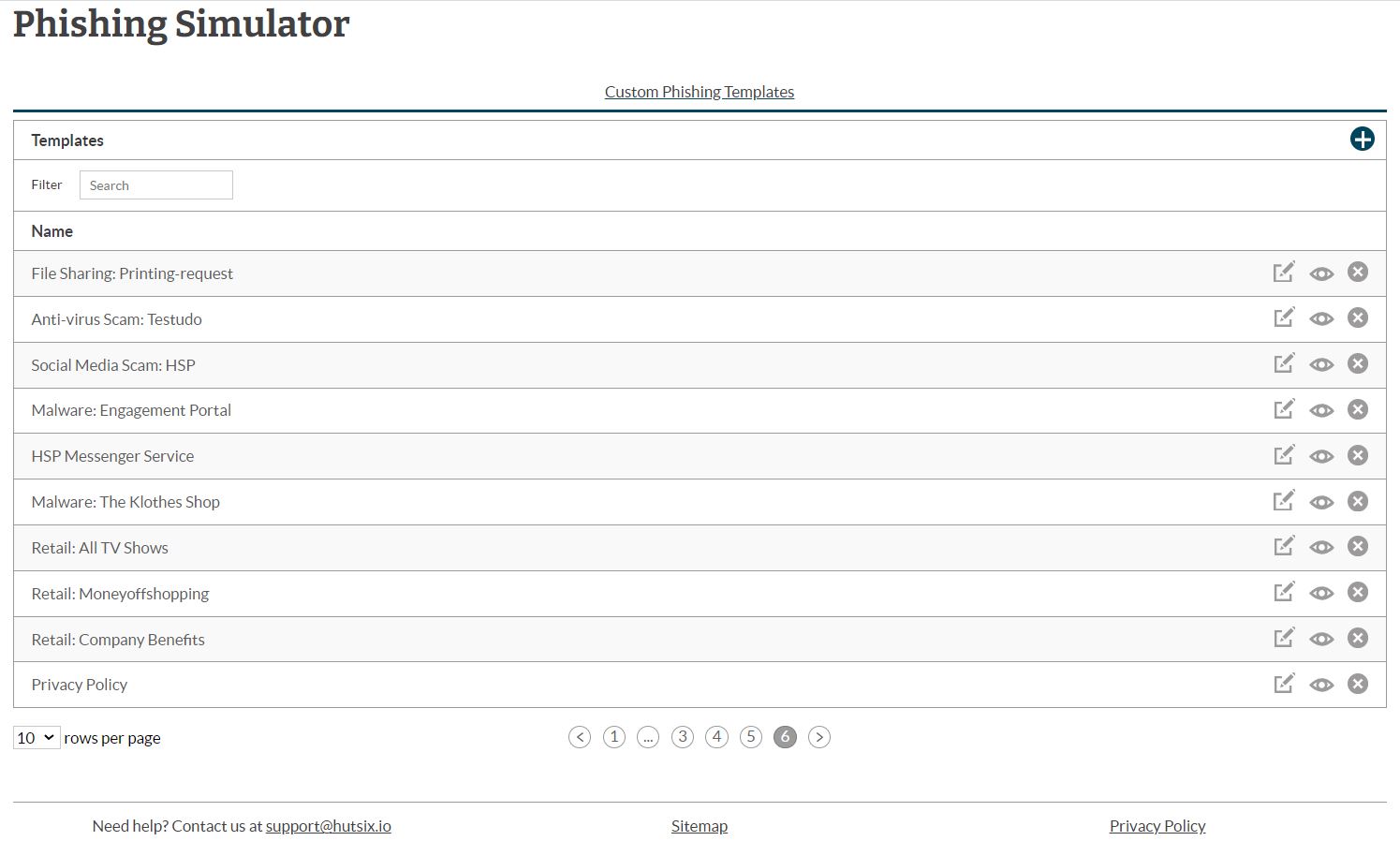
Easily edit and customise template elements with minimal effort, saving you time and energy. All without the need for any existing design experience or expertise. Or even start from scratch and build your own phishing emails from the ground up.
Search our ever-growing library of customisable templates by theme or topic. Looking for a phishing template designed to test malware-themed attacks? No problem. Or perhaps you want to discover if employees are susceptible to insurance-based phishing attacks? We have templates for all kinds of campaigns.
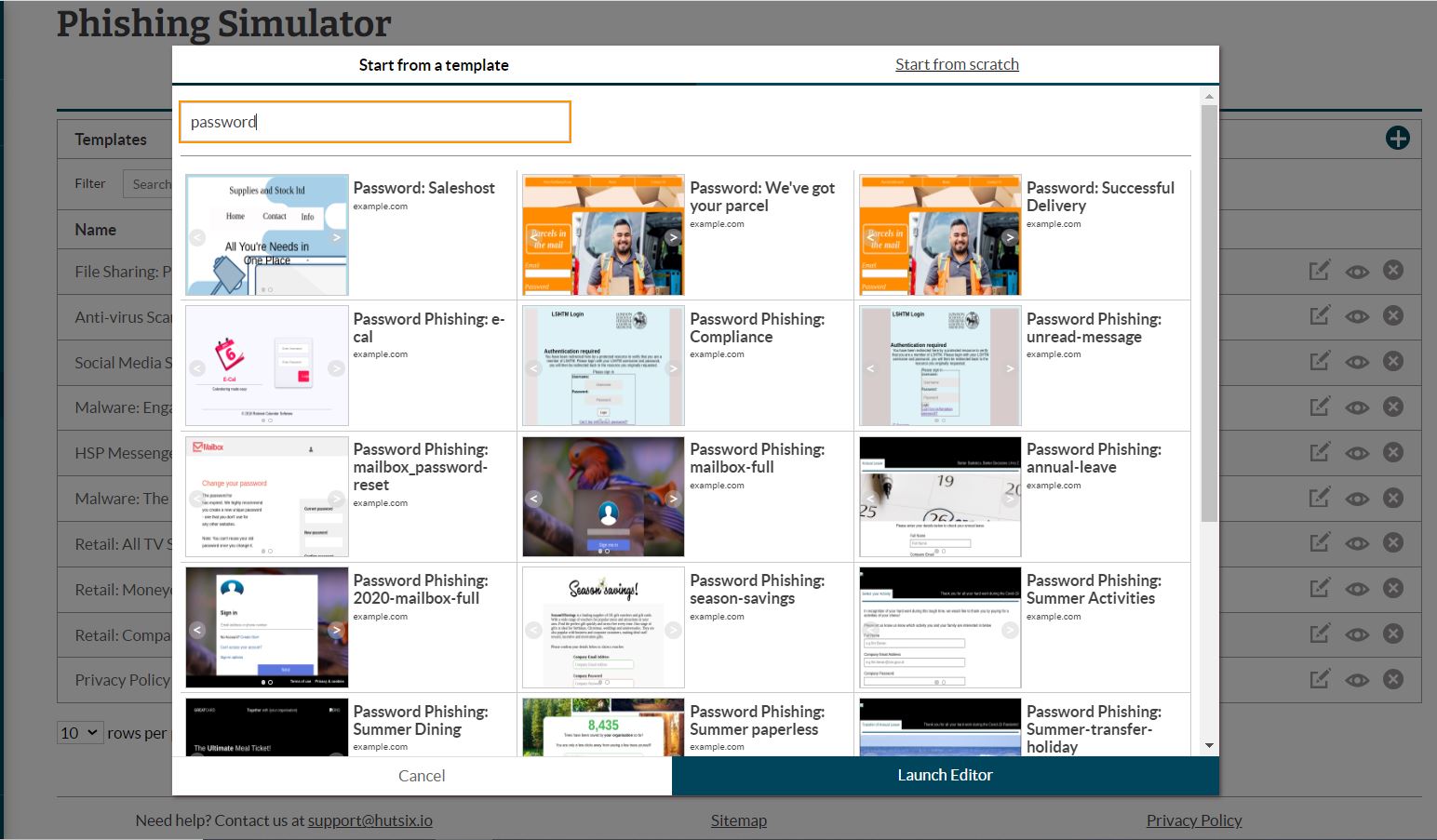
For those who are more technologically inclined, you can add further customisation by adding custom HTML and CSS – all within the Hut Six phishing editor.
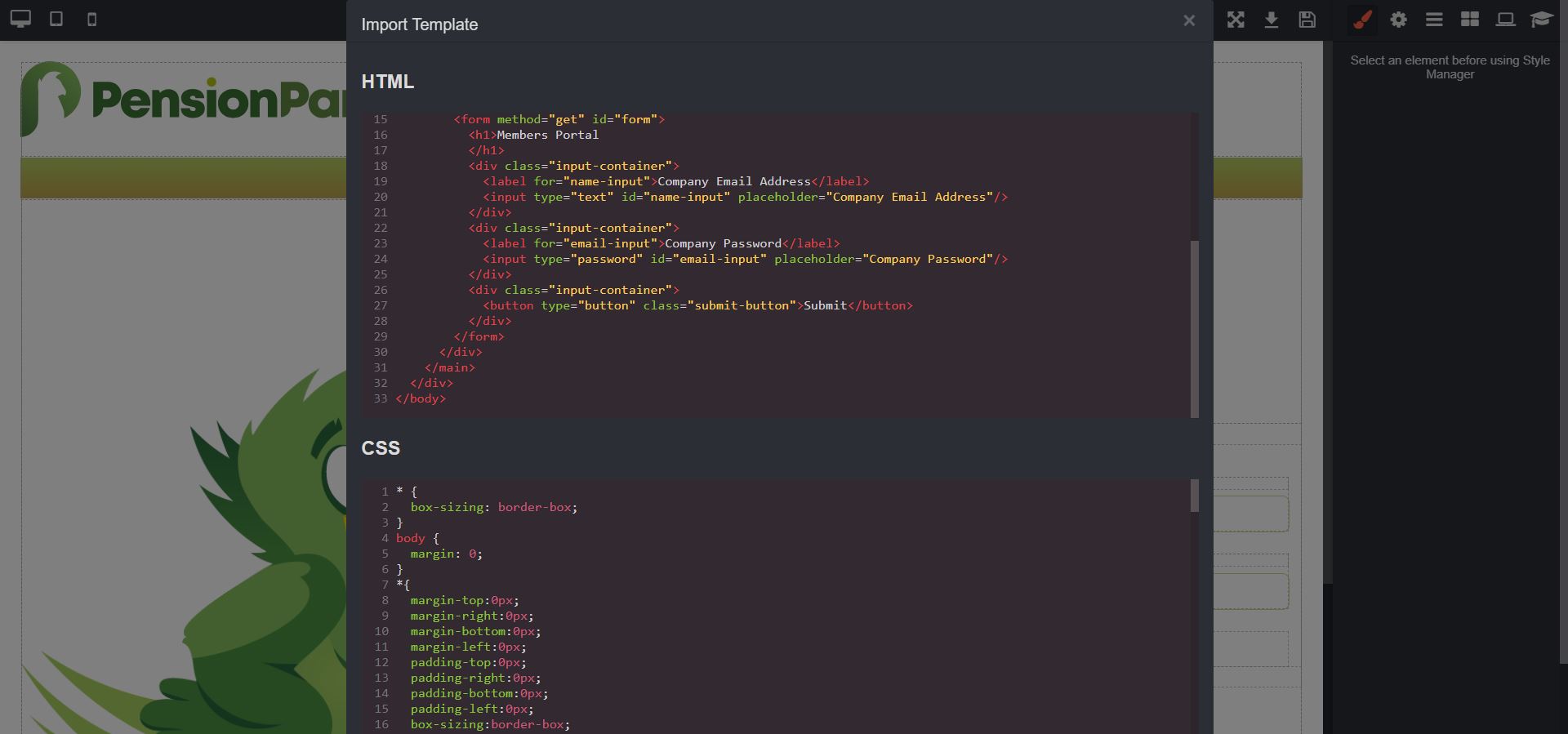
As well as generating convincing and highly customisable email templates, use the same tools to choose or build corresponding landing pages to test users ability to spot phishing websites.
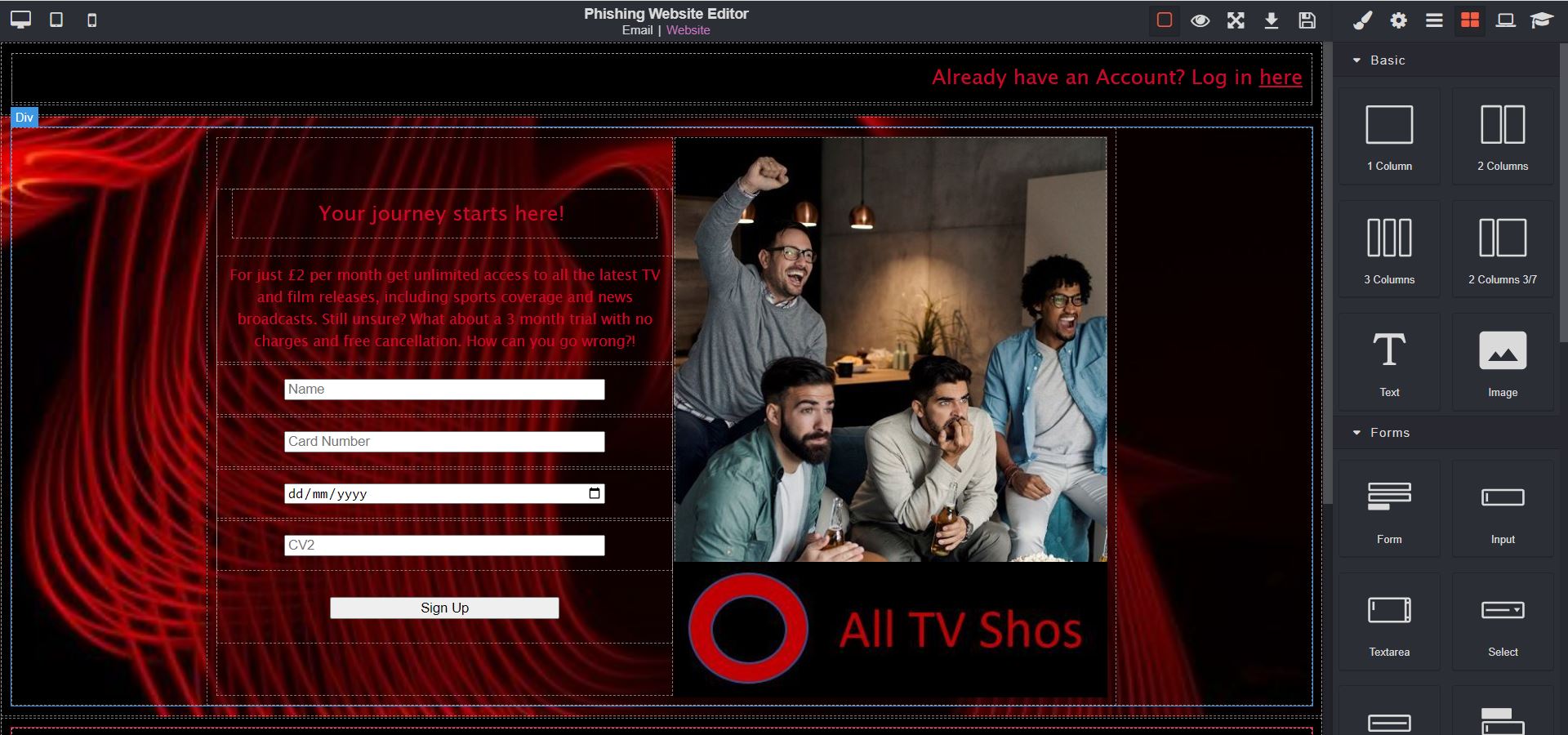
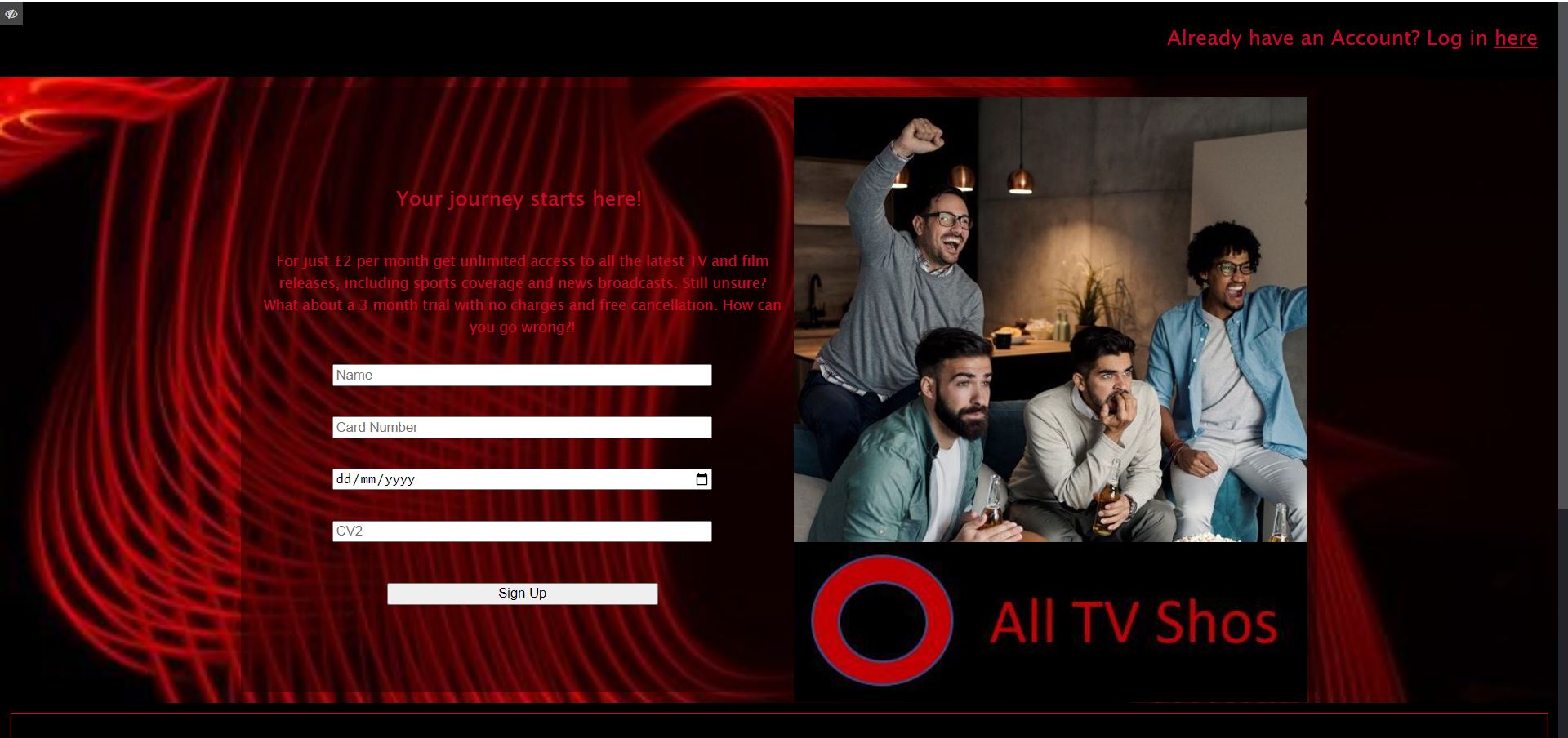
Also, you can edit and deploy simple and effective on-the-spot training pages for when users fall for your simulated attacks. Providing users with immediate feedback highlighting where they went wrong, and how they can improve their security behaviour in the future.
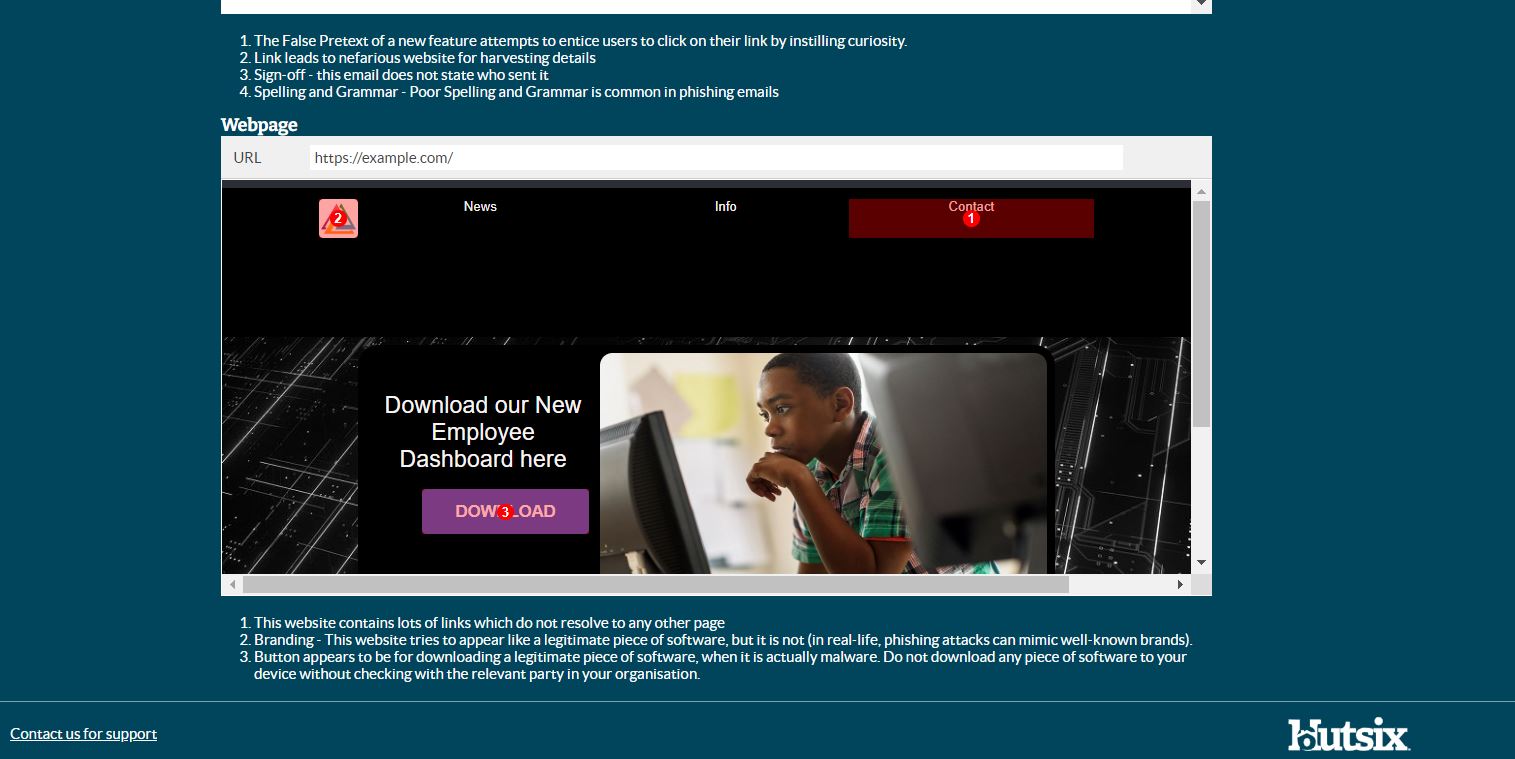
If that wasn’t enough, you can also preview your customised phishing emails before you send them to employees or users, either from inside the phishing editor itself, or by sending the email to a chosen address.
Finally, for those wondering how emails created within the phishing editor will be rendered across different email clients, Hut Six’s phishing editor is powered by MJML (or Mailjet Markup Language), meaning that whatever email client your organisation uses, you can be sure of responsive and consistent appearance.
Security Awareness for your Organisation
Enjoyed our blog? Learn more about how Hut Six can help improve you security awareness with training and simulated phishing. Start a free trial now, or book a meeting with one of our experts.
Featured
What is the Impact of Security Awareness Training? - Hut Six
Discover the Impact of Security Awareness Training: Prevent breaches, foster culture, & build trust.
What is Personal Data?
Learn about personal data, its types, and significance in data protection. Explore general and special category data, as well as pseudonymised and anonymised data under the GDPR.
Who Does GDPR Apply To?
Who Does GDPR Apply To? And Other Data Protection Questions/ Information Security blog by Information security awareness provider Hut Six Security.
Does ChatGPT Pose a Cybersecurity Risk
In this blog post, we explore whether AI chatbots like ChatGPT pose a cybersecurity risk. We delve into the potential vulnerabilities and threats posed by chatbots, and discuss measures that can be taken to mitigate these risks. Read on to discover how you can ensure the security of your organisation's chatbot interactions.
How Do I Get Cyber Essentials Certified?
Learn how to obtain Cyber Essentials certification and enhance your organization's cybersecurity posture with our comprehensive guide. Our expert insights will help you navigate the certification process to meet the requirements for Cyber Essentials.
Essential Steps for Security Awareness Training
Starting a security awareness training campaign? Here are 5 essential steps to help ensure information security success.
Malicious Insider Threats - Meaning & Examples
Malicious insider threats can cause massive problems. Here we examine some of the motivations behind attacks and methods of detection organisations can use to reduce risk.
5 Biggest Breaches of 2022 (So Far)
Five of the biggest and most significant data breaches, hacks, and information security attacks of 2022 (so far).
Auditing for GDPR Compliance
Questions to consider when auditing your business or SME for General Data Protection Regulation (GDPR) compliance.
Improving Employee Cyber Security
With human error responsible for many breaches and attacks, we offer some helpful areas for improving employee security compliance.










