Writing a Cyber Job Specification
2020 has presented many challenges for the cyber security profession, from dealing with new and evolving threats, to migrating entire organisational systems almost overnight. In many ways, the industry has risen to the challenge, though one issue that organisation consistently struggle with is finding the right people with the right skills.
In the last year, the global cybersecurity workforce grew by around 700,000 professionals, closing the industries deficit to a still substantial 3.12 million; leaving companies looking to expand their cyber team in a better position than they were twelve months ago, though still in a seller’s market.
In the UK, 42% of organisations reported plans to increase the cyber teams, a fundamental part of which is writing a cyber job specification that will attract the right candidate and the right skills to fit your organisational needs.
Be Specific but Flexible
Depending on the role for which you are writing a cyber job specification, it pays to be specific about the skills which are essential. Making sure that these key skills are clearly iterated in your job specification and not buried in the small print allows potential applicants to immediately understand what is expected.
Amongst other things, most cybersecurity job skills will include:
- Ability to analyse, diagnose, and detect security risks
- Understanding of network architecture
- Secure software development skills
- Up to date knowledge of news and developments in cybersecurity
- Communication and collaboration skills
- Cybersecurity awareness
Clearly indicate which skills are essential, and which may be desirable; as well as explaining that if a candidate possesses additional skills that may be relevant, such as unique training or abilities, this information should also be included in an application.
Realistic Expectation
If you happen to be connected to any recruiters on LinkedIn, or have spoken candidly to those looking for work inside the industry, you may have noticed that cyber security job specifications often place unrealistic expectation on the knowledge and experience needed for a role.
We have seen example of companies asking for 10 years plus experience for entry level roles. To readers, this will make a recruiter look amateurish, and will quite frankly, ultimately discourage more discerning potential applicants.
Provide Ways for Candidates to Stand Out
As with many professions, a potential candidate may on paper appear highly skilled, highly credentialed and well suited for the role; though by the interview stage of hiring, this same person can just as easily turn out to be incurious, be lacking in passion and simply not right for your company.
When thinking about how to write a cyber job specification, think about ways in which you can encourage an applicant to show you some of these vital characteristics in the beginning stage of your hiring process.
For a relatively entry level role, you’re probably not looking for a candidate with years of experience or multiple PhDs, but rather someone who enjoys challenges, problem solving and has a practical, creative and methodical approach to developing skills.
Autodidacts, or self-learners, with a real drive for understanding may not always stand out when responding to a basic cyber job specification, so even simply asking ‘what areas outside of cybersecurity interest you?’ may be enough to allow an unconventional candidate to stand out of the crowd.
Do Not Overthink It
When considering how best to write a cyber job specification, an often-overlooked element is simplicity. Take a look below at the first job specification posted by Amazon’s Jeff Bezos. It’s clear, simple and gets right to the point.
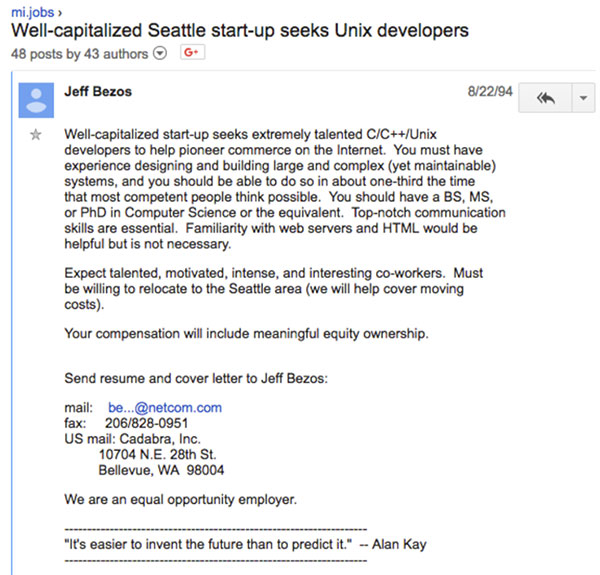
This is not to say your finished cyber job specification should look exactly like this, but consider what needs to be communicated, and what can go unmentioned.
Allow Your Organisation to Stand Out Too
With the industry as it is, with many organisations desperate for new talent, it is not just a candidate that needs to stand out. When thinking about how to write a cyber job specification, you don’t just want a candidate to demonstrate their value to you, but for you to also demonstrate your value to them.
Read More: How to Build a Cyber Team - Top 5 Points to Consider When Building Your Team
Whatever your company does and however it operates, there are elements that make it unique. Take the time to find the best ways of communicating what makes your organisation special, its values and its mission statement.
Even if this means getting a little extra help from your marketing or communication team in articulating this, by presenting your organisation in the best possible light, this step will help ensure you are attracting candidates that are likely to fit with your company culture.
Think beyond what you offer in terms of remuneration. With an increasing portion of professionals working remotely, a sense of being part of a common goal and a strong, focused team can easily be lost. Touching on what your organisation does to ensure a positive work and home life balance or to instil an internal community, may be what sets your team apart from others.
Security Awareness for your Organisation
Enjoyed our blog? Learn more about how Hut Six can help improve you security awareness with training and simulated phishing. Start a free trial now, or book a meeting with one of our experts.
Featured
How to Build a Cyber Team
How to Build a Cyber Team - Top Points to Consider When Building Your Team. Blog by Information Security Awareness solution Hut Six Security.
What is GDPR Compliance UK?
What is GDPR Compliance UK? Understanding the General Data Protection Regulation and UK Compliance. Blog by Hut Six Security.
What is a DDoS Attack?
What is a DDoS attack and what should you do if you think you are experiencing one? Blog by Information Security Training provider Hut Six Security.
Does GDPR Apply to Individuals?
Does GDPR Apply to Individuals? How GDPR Relates to you Personally. Blog by Information Security Awareness Training provider Hut Six Security
Does GDPR Cover Paper Records?
Does GDPR Cover Paper Records? Paper Records and Data Protection Law blog by Information Security Awareness Training provider Hut Six Security.
How Secure is My Organisation?
How Secure is My Organisation? Knowing where you are, before knowing where to begin. Blog by Information Security Awareness solution Hut Six Security.
How Does Ransomware get on your Computer?
How Does Ransomware get on your Computer? Chances are that in the last few years you've heard the term "ransomware". Blog by Hut Six Security.
Guest Blog: How to Audit Your Business for GDPR Compliance
How to Audit Your Business for GDPR Compliance with a GDPR Business audit. Hut Six Security guest blog by https://reciprocitylabs.com/.
What is a Breach of Data Protection?
What is a Breach of Data Protection? The Data Protection Act - Personal Data Breaches, Reporting and Consequences. Blog by Hut Six Security
University Hit With $1.14m Ransomware Attack
University of California Ransomware Attack: a $1.1.4m ransom has been paid following a ransomware attack on University of California's School of Medicine.










