Ransomware Propagation
How to be Protected from Getting Infected
Probably on the news, maybe in information security training, possibly from being infected yourself; no matter where or who you are, chances are that in the last few years you’ve heard the term ‘ransomware’.
Despite frequently being in the news (WannaCry, Travelex), most users don’t have a great understanding of how to protect themselves, and many businesses still not understanding its seriousness. Malware is no longer just an obscure security threat and users are reasonably asking, what is ransomware and how does ransomware get on your computer?
Luckily, we’re here to help, with a comprehensive guide including explanations of important terms, an overview of the history of ransomware, the various categories and differences between ransomware strain, and tips and advice of how to avoid and defend against malicious software.
What is Ransomware?
Ransom malware, usually known as ransomware, it a category of malware (malicious software) that is designed to hold a user’s data to ransom. Having infected a computer, ransomware encrypts files while demanding a payment for its possible decryption.
Basically, a digital hostage situation.
Having been around almost 30 years, ransomware is now a booming industry with a significant portion of businesses across the world being targeted for attack. With the mainstreaming of blockchain technology and anonymised transactions, ransomware con artists frequently demand payment for decryption in difficult to trace cryptocurrency.
Faced with the choice, many companies and businesses are choosing to discreetly pay these ransoms to re-establish access to their data, whilst some fight to reclaim data without paying attackers. Either way, there can be substantial damage done, not only financially, but operationally and reputationally too.
History of Ransomware
Though the notoriety of ransomware has undoubtedly exploded in the 21st century, ransomware in fact dates back far longer that many may assume. With the sophistication of modern ransomware, it may strike some as comical that the first example of this kind of malware was distributed via floppy disk.
Originating in 1989 and designed by an evolutionary biologist by the name of Joseph Popp, the nefarious Harvard PhD researcher loaded up around 20,000 floppies with copies of the ransomware and distributed them to other scientific researchers in 90 other countries.
Disguised as a questionnaire, the ransomware was obfuscated by means of an electronic ‘fuse’. Once the ransomware had infected a computer, it would lay dormant within the system until the 90th boot. Once the computer was switched on for the 90th time since infection, the ransomware would encrypt file names, a technique which may not sound that lethal now, but at the time left many computers unusable.
Demanding the user to pay a supposed ‘hard drive lease’ (between $189 or $378), the ransomware message commanded the ransom be sent in the form of a cashier’s check or money order to a Panamanian P.O box register under the name PC CYBORG CORPORATION, if they were to ever receive their decryption key.
Though it remains unclear exactly how much was successfully extorted, the ‘eccentric’ Popp was eventually caught by the FBI. The arrest likely as a result of a luggage search, which turned up his ‘corporate insignia’; Popp was eventually extradited to Britain on ten counts of blackmail and criminal damage.
*Fun Fact* Popp now operates a butterfly conservatory in New York. Trip Advisor here.
It was not for another decade that fellow cyber-criminals were to take the blueprint created by Popp and deploy it at a much larger scale. Minus the floppy discs and P.O Box, most criminal ventures still operate in largely the same way. Distribute, infect and extort.
By the mid-two thousands, ransomware had become a significant threat and strains such as TROJ.RANSOM.A, Krotten, Cryzip and Gpcode were starting to become commonplace. By the end of that decade and into the tens, the sophistication and effectiveness of ransomware really began to develop.
With the international effects of worms such as the WannaCry virus (which cost the UK’s NHS around £92 million) and the black-market trading of ‘malware as a service’, the costs and likelihood of ransomware infection has continued to grow, unsurprisingly outpacing awareness.
We now find ourselves in a place where, should an organisation be locked out of its systems without backups, they are faced with the choice of either handing over thousands of pounds in cryptocurrency to criminals (funding further attacks and with no certainty of a decryption key), or accept the invariably much larger cost of recovery.
Case Study
In 2019, cyber-criminals managed to infect around 10,000 Baltimore city computers with ransomware known as RobbinHood. Having demanded 13 bitcoins (around $76,000) for their decryption, the attackers were refused their ransom when city officials took advice not to contribute to the criminal enterprise.
Instead choosing to fight the infection, it’s estimated that the damage caused by the ransomware attack has cost the city upwards of $18 million in recovery. An amount mirrored in similar situations.
This being the case, it is indeed ill judged for organisations to continue to put themselves at risk of infection by not offering the adequate cyber and information security awareness training necessary to help mitigate the risk of becoming another ransomware victim.
How Does Ransomware get on your Computer?
Like all digital nasties, there are many ways that ransomware can make its way onto your computer, though similarly, most of these entry points can be defended with basic education and simple defensive techniques. Keeping your files secure and protected from ransomware doesn’t need to be a huge hassle, nor does it need to cost the world.
The below are just some of the most common ways that ransomware contaminates a computer. With ever more advanced and improved upon technological mechanisms, the routes that most malware takes to infect a computer, have remained relatively constant.
Phishing
Usernames, passwords, bank details and credit card numbers, all of which are gold to cyber criminals everywhere. Phishing emails are fraudulent messages sent with the express intent of manipulating users into executing a certain action. These actions can include following a link, handing over sensitive information, or in the case of malware, typically opening an attachment.
Phishing attacks are a type of blanket attack, sent out to millions of users with the intent of attracting as many ‘biters’ as possible. Varying wildly in sophistication, phishing messages usually seek to imitate well-known brands, trusted organisations, or capture your interest or curiosity with eye catching subjects and deceptive attachment names.
Regardless of the appeared legitimacy of an email, SMS or even snail mail, individuals should always be wary of handing over sensitive information to dubious parties or opening unverified attachments. What you think is an innocuous PDF attachment, may easily be a malicious piece of software, specifically designed to hold your important data hostage.
Spear Phishing
Spear phishing is a form of phishing which, like its fishing analogy, is a highly targeted campaign. As a far more sophisticated and research dependant form of phishing, spear phishing attacks frequently target the financial departments of organisations and businesses.
By imitating or indeed compromising legitimate accounts, a spear phishing attack will often go to great lengths to deceive users into executing an action that plays directly into the hands of criminals. Attacks will often intercept large transfers of funds, with account numbers being changed at the last moment and forged invoices.
Like phishing attacks, spear phishers will often be on the lookout for sensitive information, anything that could help them deceive and trick. With more time and effort invested, spear phishing can not only prompt fraudulent transfers, but may also seek to infect highly guarded networks with ransomware, with the hopes of extorting large sums of money for the return of data access.
Social Engineering
As a kind of catchall term, social engineering refers to both in-person and remote manipulation. Attacks will use their skills of manipulation to guide unsuspecting targets into performing an action which is against their own interests. This can be as seemingly rudimentary as pretending to be someone else, to the technically skilled appropriation of an email account and the carefully timed transfer of funds request to the financial department.
Social engineering may encompass ‘phishing’, ‘spear phishing’, ‘water holing’ and a whole manner of other techniques, but this ‘low-resolution’ attack vector should not be dismissed as not specific enough, and should be appreciated as a recognisable category which people and users should be aware and vigilant of.
By being conscious of the various ways in which even the best of us can be manipulated, awareness allows us to better defend against a wide spectrum of attacks. At a time when attacks are always looking to find new ways to exploit our information, appreciating and acknowledging weakness is paramount.
Case Study
In 2016, members of a Google research team conducted a social engineering experiment. Scattering 300 USB sticks around a university campus, they found that 45% of drives were plugged in and had files examined.
Though, in this instance a harmless experiment, the devices could have just as easily contained ransomware. Left in the right place, malicious actors could exploit this insecure curiosity to bypass network defences and lock away vital data.
Types of Ransomware
The information security threat that ransomware poses invariably contains a similar set of features. A ransomware attack can not only compromise the availability of your data, but its confidentiality and integrity too.
Following the infection of your device, ransomware will likely follow one of only a few possible paths. Having either locked a user from accessing their device, or encrypting documents contained within, the attacker(s) will then attempt to extort a payment by threatening either the deletion, indefinite encryption or the public exposure of your data, depending on the nature of the attack.
When targeting businesses, attacks will most often threaten the deletion or indefinite encryption of data, whereas in attacks on individuals, criminals will threaten making public some sort of embarrassing or compromising data.
A deadline for ransomware payment is one way that attacks motivate victims to pay. For example, should a ransom of ‘X’ not be pay within 48 hours, then the ransom will increase to ‘2X’, and exponentially thereafter. By paying immediately and without complication, an organisation can hopefully recover their data in a short a time as possible, and for the smallest cost; though payment is rarely recommended by law enforcement entities.
How Does Encryption Work?
Encryption is the process by which information is encoded, such that it can only be viewed by those in possession of the correct ‘key’. Though this process now uses complex mathematics to obfuscate information, even the most primitive examples follow the same basic principles.
At its core, the process of encryption takes a piece of information, let’s say the word ‘hello’, and seeks to disguise its meaning. If we take one of history’s oldest examples of encryption, known as the ‘Caesar Cipher’, all we need do is transpose each letter 3 letters further along in the alphabet. Now only those who know the ‘cipher’ or key, know what we mean when we say ‘khoor’.
Despite not always being an obvious element of our everyday lives, encryption is a process that is essential to modern communications. From the messenger apps on your phone, to the sensitive information you enter into a website to pay for your package, encryption is a vital component of modern computing.
Though encryption is typically used to keep our information safe, it can also be exploited to cause us harm. In the case of ransomware, cyber criminals utilise methods of encryption to take information hostage and extort payments. Once relatively easy to defend against, ransomware is at the point when even the most safety conscious and well-funded organisations can fall prey, and as a result, sometimes even collapse.
Ransomware Examples
CryptoLocker
Active between 2013 and 2014, the CryptoLocker ransomware spread via infected email attachments. Once active, the malicious software sought out important files to encrypt and ransom.
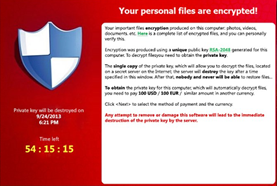
Estimated to have infected around half a million computers worldwide, the ransomware targeted Microsoft Windows machines, using an RSA 2048-bit key to encrypt important files.
With this level of encryption, users without file backups had the choice to either accept the loss or pay the ransom.
Estimated to have extorted an average of $300 per user, CryptoLocker likely earned the criminals behind the campaign tens of millions of dollars in a matter of months. Despite causing a considerable amount of trouble for many users, an online tool was eventually created to distribute decryption keys to victims of the ransomware.
Petya
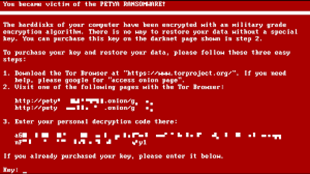
Unsurprisingly distributed via infected attachments, the Petya family of ransomware was first detected in 2016.
Perhaps most known for its involvement in attacks on Ukrainian infrastructure, many variations spread across the world, including the Kaspersky named NotPetya.
As well as affected infrastructure, the NotPetya strain is also responsible for one of the most notable attacks on a law firm. The DLA Piper attack is reported to have resulted in the company paying out around 15,000 hours of overtime for IT staff, as well as immeasurable damage being inflicted upon its reputation.
Chief Information Officer, Don Jaycox stated that the ransomware had spread at an “astonishingly fast” rate, adding "a lot of the damage was done before [he] even got out of bed."
Ryuk
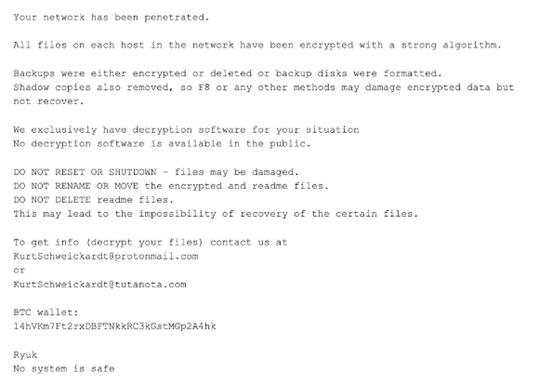
Hitting the threat landscape in 2018, the Ryuk ransomware strain almost exclusively targeted large organisations, with ransoms of up to $320,000. Spreading to as many endpoints as possible, this strain was again likely spread through the common attack vector of phishing emails.
Continuing to affect organisations to this day, Ryuk’s ransomware victims include, amongst others, US government contractor Electronic Warfare Associates (EWA).
The proliferation of the ransomware continued until in Q4 of 2019 the malware represented a massive 21.5% share of the ransomware market.
Ransomware and your Business
With some research suggesting that the average cost of a data breach has now skyrocketed to $3.9 million, the impact of data breaches, including ransomware, can no longer be ignored by businesses. Beyond the obvious cost in recovering from a ransomware attack, an incident such as that can also inflict untold damage from disruption to services and a loss of reputation.
In the UK, a shocking 77% of all UK workers have never received any form of information security training from their employer; a flagrant disregard for security awareness that makes it all the easier for hackers and cyber criminals to continue their malicious campaigns.
With the introduction of the European Union’s General Data Protection Regulation, as well as its adoption into UK law as the Data Protection Act (DPA) 2018, it is possible for the enforcement authority, the Information Commissioner’s Office to impose penalties upon organisations found to be responsible for a breach of personal data, of up to 4% of annual global turnover, or 20 million Euros, whichever is greater.
Meaning, not only could a ransomware attack cost an organisation millions of pounds to technically recover from, but also cost them even more in non-compliance fines. Considering all these factors, it’s reasonable to say, it has never been more business critical than now to seriously address information security issues within your organisation.
Protecting Against Ransomware
Backing Up Data
The success of a ransomware campaign relies on two fundamental assumptions. Firstly, that the ransomware will successfully infect a computer and secondly, that important files won’t be backed up. Attackers and criminals rely on businesses and individuals lacking the basic preparation for fending off an attack and thrive on common mistakes.
By adequately backing up your data in separate, secure forms and locations, your business can strengthen your defences and help ensure that if the worst does happen, you’re not backed into a corner and forced to decide between further funding criminality, or accepting the costs of starting again and a full recovery.
There are plenty of precautions and options that businesses and individuals can take to defend against ransomware. The most simple and effective of which is frequent and secure backups. Redundancy is the name of the game, with information needing to be kept, when at its most vital, in multiple locations, as to protect against physical damage such as floods, break-ins, fires etc.
Cloud storage services can also offer an effective solution to your backing up needs. By keeping data off-site and in secure networks, cloud storage can, in many cases offer a suitable alternative to on-site backup storage.
Patches and Updates
One of the contributing factors that made the NHS so susceptible to the WannaCry ransomware, was that many of the computers in use were running out-of-date operating systems and unpatched software. These weak systems were not protected in the same way current operating systems typically are, and this vulnerability left the door open to a cyber-attack.
With all operating systems, it is paramount to ensure that the software (especially the anti-virus) being used is the latest version and fit for your purposes. New vulnerabilities are discovered every day and developers work hard to ensure these issues are patched and fixed, though when these updates are not made, organisations are susceptible to attack.
Preparing Staff
The most vital weapon in your defence arsenal can be your workforce. Though technological defences undoubtedly play a role, when the vast majority of ransomware, and indeed all information security attacks, are as a result of human error, it’s obvious that comprehensive information security training is one of the most effective ways of sharpening your defences.
With engaging training, your organisation’s defences are strengthened against malicious actors, reputational damage and potential fines and losses, whilst also satisfying compliance obligations.
What to do if you get Infected?
The unfortunate reality regarding many ransomware attacks is that affected organisations frequently pay, often not insubstantial sums. Despite official guidance invariably advising organisation to never pay the ransom to regain access, it is often practicality and costs that guide the decision to hand over the cash.
Holding an organisation hostage with ransomware is a crime and should be reported as such; though with the use of cryptocurrency and obfuscation techniques attackers are rarely caught. Another disheartening reality within the fields of information security and cyber defence.
Isolate > Identify > Report > Research and Restore > Resume
Providing you have sufficiently backed up your data, restoring operations should be reasonably straightforward. If you have failed to back up, the situation becomes significantly more complex.
Once a ransomware attack has struck an organisation, depending on the type of ransomware, much of the process will likely require skilled technicians and cyber security experts. Saying that, with many of the more archaic strains of ransomware, decryption keys can be found online, typically at no cost.
Reporting a Ransomware Attack
Under the UK’s Data Protection Act (DPA) and the EU’s General Data Protection Regulation (GDPR), should any sort of breach occur, including a ransomware attack, wherein personal data is unlawfully destroyed, lost, altered or been disclosed without authorisation, then you likely have a legal obligation to report this event to your specific enforcement authority (in the case of the UK, the Information Commissioner’s Office).
Reporting Regulations
- An organisation is required to report a breach of personal data to the relevant supervisory authority within 72 hours of becoming known (where feasible).
- If the breach is likely to result in ‘adverse effects upon the rights and freedoms of data subjects’, those individuals must be informed ‘without undue delay.’
- You must also ensure there are “robust breach detection, investigation and internal reporting procedures in place.”
Hut Six Information Security Awareness Training
Featuring twenty-six comprehensive tutorials covering all aspects of information and cyber security, Hut Six’s training is focused on demonstrating learning outcomes. With Hut Six’s learning management system (LMS), employers can assess and track the achievements of staff and better understand areas for improvement.
If you’d like to learn more about how you can protect your greatest assets with unique and engaging information security awareness training, click the link below.
Finding training that helps build a comprehensive solution to the issue of human error, also allows an organisation to not only mitigate the risk to information security, but also allows a business to avoid the reputational damage that comes with a data breach. Not to mention the large fines that are now levied against organisations in violation of data protection.
Security Awareness for your Organisation
Enjoyed our blog? Learn more about how Hut Six can help improve you security awareness with training and simulated phishing. Start a free trial now, or book a meeting with one of our experts.
Featured
Guest Blog: How to Audit Your Business for GDPR Compliance
How to Audit Your Business for GDPR Compliance with a GDPR Business audit. Hut Six Security guest blog by https://reciprocitylabs.com/.
What is a Breach of Data Protection?
What is a Breach of Data Protection? The Data Protection Act - Personal Data Breaches, Reporting and Consequences. Blog by Hut Six Security
University Hit With $1.14m Ransomware Attack
University of California Ransomware Attack: a $1.1.4m ransom has been paid following a ransomware attack on University of California's School of Medicine.
What is the Purpose of the Data Protection Act?
What is the Purpose of the Data Protection Act? Blog by information security awareness training solution provider Hut Six Security.
Top 3 Remote Work Security Lessons
Top 3 Remote Work Security Lessons: remote work security blog by information security awareness provider Hut Six Security.
Who Regulates the Data Protection Act?
Who Regulates the Data Protection Act? Data Protection Blog by Information Security Awareness Training provider Hut Six Security
NHS Email Accounts Compromised in Phishing Attack
NHS phishing attack sees email accounts compromised as part of an attack targeting a wide range of organisations Blog by Hut Six Security.
Who Enforces the Data Protection Act?
Who Enforces the Data Protection Act? Principles, Protections and Penalties. Blog by Information Security Awareness Training provider Hut Six Security.
How Secure is Your Password Process?
How Secure is your Password Process? Password security blog from Information Security Awareness Training provider Hut Six Security.
Who Does the Data Protection Act Apply To?
Who Does the Data Protection Act Apply to? Blog by Information Security Awareness Training and phishing simulator provider Hut Six Security










