Phishing Text Message Examples
How to Detect, Report and Block Smishing Attacks
Just as you’ve likely received your fair share of scam emails, chances are you’ve also received some suspicious text messages. Every year, an almost incalculable amount of funds is lost to online frauds, scams and brazen criminality, and although the majority of these are sent via email, SMS based phishing is still a significant information security threat. What is a phishing text message? Read on to find out more.
What is a Phishing Text Message and What is Smishing?
Derived from the combination of SMS and ‘phishing’, smishing attacks rely on the same basic principles as email phishing attacks. They are a form of inauthentic communication specifically designed to extract sensitive information from targets, to be used and exploited, invariably for financial purposes.
Like phishing emails, smishing attacks often seek to impersonate a known or trusted organisation to fool a victim into a false sense of security. Often it is through links that redirect a user to an inauthentic or ‘spoofed’ website that may appear legitimate, yet is merely designed to harvest login credentials, passwords and other sensitive info.
Why Scammers are Targeting SMS?
Despite being nothing new, there are certain elements of smishing scams that have over recent years become more sophisticated, more difficult to spot and on occasion, more persistent. The reality is, scammers will, given enough time, try any and all methods to get the sensitive information they’re after.
One of the reasons that smishing may be becoming more of a common threat is our increased reliance upon 2 factor authentication (2FA) to secure accounts. This security protocol perhaps means some of us are becoming habituated to instinctively trusting SMS communication as a safe method of verification.
Though 2FA is designed to make us more secure, because the security of our channels of communication are become defused, scammers and fraudsters are energised by the potential of smishing for extracting sensitive information. Applying the same tactics from many email-based phishing attacks, your phone is just as good of a target as your computer.
Another reason why criminals may be eager to target phones is that when a user follows a link (included within the smishing message), the URL which displays within the typical phone browser is ‘truncated’ and betrays far less information than a normal computer browser.
3 Easy Ways to Spot Fake Scam Text Messages
Having asked yourself "what is a phishing text message?" and familiarised yourself with the background to what smishing is and why scammers use it, the next step in tackling the problem is arming a user with the tools to both identify and avoid the information security threat of smishing attack.
As with phishing emails, there are often elements of the communication that can be looked out for that will help you differentiate the fakes and the frauds from the trusted and genuine. Though this will add a few seconds to most of your communications, it’s undoubtedly worth the extra time to avoid accidentally handing over social media passwords, bank details, or even your identity.
Lack of Specifics
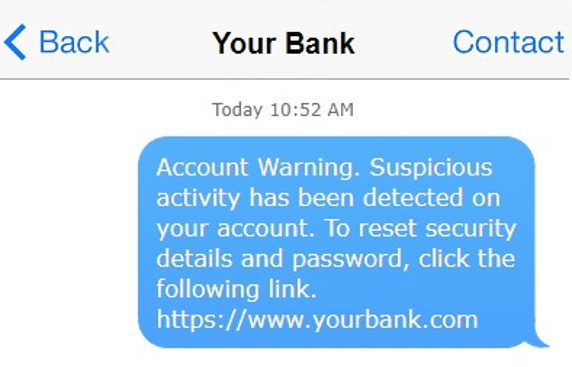
Illustrated left, one feature which can expose a smishing attack is a lack of specific details. Given that many of these SMSs are sent out to thousands if not millions of numbers, scammers often attempt to cast as wide a net as possible by making their attacks generic.
Suspicious Links
Much of the time, a legitimate piece of communication will deliberately make sure any address contained will be shown in full and avoid URL shortening. As shown below, scam text messages will do the opposite, as often the full address is immediately more suspicious that the obfuscated alternative.
If you’re unsure about the legitimacy of a message, open your browser separately and find the supposed page through the organisation’s website, or through a trusted search engine. By following a link, you don’t always know where you are going to end up.
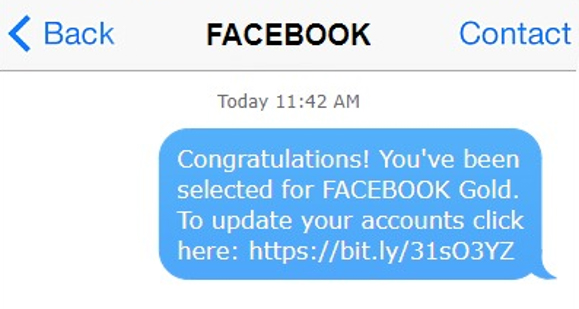
Too Good to be True
You have won! Most forms of social engineering, which includes phishing, rely on several specific and reliably exploitable traits: curiosity, generosity, laziness, and in this case, greed. Playing to these human weaknesses is an age-old technique which far predates digital communications (and will likely outlast them too).
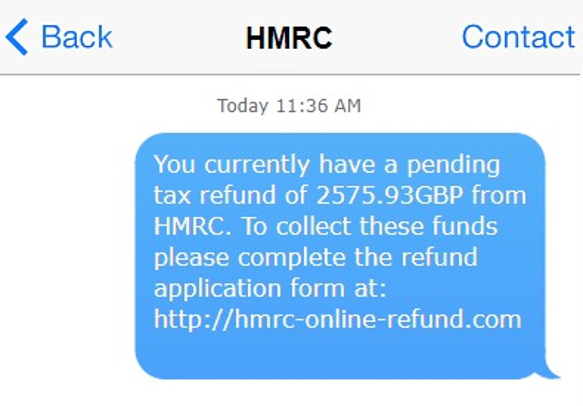
Whether it’s prize money from a lottery, an unexpected tax refund, or a friendly Nigerian prince, chances are, these messages are not looking to give you anything, but rather take as much as they can.
If you do happen to enter a lot of competitions in which you hand over your phone number, it’s probably a good idea to keep a note of the organisation’s details, and only transmit sensitive information through verified channels.
Blocking and Reporting Phishing Text Messages
Blocking SMS Phishing
Depending on the type of device you use, there are likely several steps you can take to help block unknown, nuisance and scam numbers. Although these methods may not stop smishing messages completely, it should help to greatly reduce the quantity.
Firstly, if you are using a smart phone, there are typically setting that can be toggled to reduce the amount of numbers allowed to contact you. For example, for iPhones: Settings > Messages > Filter Unknown Senders. (To find your devices options, search the device name and “block unknown senders”.)
Enabling this setting will place messages from selected numbers into a separate list which can be independently viewed away from your trusted contacts. Within these setting you can allow add numbers to a ‘Block List’, ensuring you will not receive message from a specific number after you recognise it to be fraudulent.
As well as this, you can head to your trusted app stored to find all kinds of applications that will help blocking such numbers. Like most anti-virus software, many of these apps rely on databases of untrustworthy numbers to aid users in avoid phishing attacks. (Note* As with all third-party applications, the time should be taken to verify the trustworthiness of the software before installation.)
Reporting Scam Texts
When it comes to smishing attacks, avoidance is your best defence, though if you wish to help others avoid similar messages or if you have been a victim of digital fraud, there are several things you can do to report text based phishing.
Most UK based networks allow you to report SMS messages by forwarding the communication and number to 7726 at no cost. These messages can also be reported to the Information Commissioner’s Office (ICO) whilst additional support can be given by National Fraud and Cyber Crime Reporting Centre (Action Fraud).
Security Awareness for your Organisation
Enjoyed our blog? Learn more about how Hut Six can help improve you security awareness with training and simulated phishing. Start a free trial now, or book a meeting with one of our experts.
Featured
Cyber Criminals Always There to Exploit a Crisis
It has been reported that a significant cyber attack has been launched against the World Health Organisation. Information Security blog by Hut Six Security.
6 Business Critical Information Security Tips for SMEs
Information security tips to help safeguard any organisation. Blog by Information Security Awareness Training Provider Hut Six Security.
The Essential Anti-Phishing Training Guide for SMEs
What is phishing and how can you avoid it? The essential Anti-Phishing Training Guide from information security awareness platform Hut Six Security.
What to Do if you Don’t Have a Business Continuity Plan
In times of sudden change, be it a natural disaster, electronic failures or global pandemics, having a business continuity plan is essential. But what should you do if you don't have one?
Phishers Exploiting COVID-19 Coronavirus
Phishing attacks are using the COVID-19 Coronavirus as a means of attracting unsuspecting individuals. Information Security blog from Hut Six Security.
SME Security is No Picnic
SME Security is No Picnic: problem in Chair not in Computer. Information security blog by information security awareness training provider Hut Six Security.
How Does the Data Protection Act Affect Businesses?
How Does the Data Protection Act Affect Businesses? Rights, Obligations and Important Concepts. Blog by Hut Six Security.
Google Warning Over Huawei Devices
Google Warning Over Huawei Devices: Huawei concerns continue. - blog by Information Security Awareness Training provider Hut Six Security
How Much Compensation for Breach of Data Protection Act?
How Much Compensation for Breach of Data Protection Act? Your Data Rights and Right to Compensation. Blog by Hut Six Security.
What is Phishing? In Computer Technology - It’s a Number 1 Threat
Phishing is a number one cyber threat, and awareness training is required to ensure all employees realise it's a business-critical matter.