Confirmation of Payee - APP Scams
In a bid to help reduce the likelihood of customers being duped into transferring funds to fraudulent bank accounts, the UK’s six largest banking groups will be implementing Confirmation of Payee by 31st March 2020.
The confirmation of payee requirement, issued by the Payment Systems Regulator (PSR), will soon obligate banks to verify account holders’ names prior to a transfer being authorised. Covering around 90% of all bank transfers, this new service has been developed to help curb the frequency of Authorised Push Payment (APP) scams for UK customers.
APP Fraud
In 2018 alone, the costs of these APP scams amounted to £228 million from personal bank accounts and £126 million from business accounts. According to research conducted by UK Finance, there were an estimated 84 thousand APP scams last year; with 92% involving personal accounts, there is currently very little protection afforded to the victims of this type of fraud.
Typically, funds transferred in cases APP fraud are not recovered by the victims, with an average loss to individuals of almost £3 thousand and little bank liability, the news of Confirmation of Payee being implemented, is something that both the general public and information security professionals should be extremely pleased to hear.
Cases of APP usually involves the intercepting of genuine payment information. Invoices and requests for payments can appear to be genuine, though it is clearly increasingly common that fraudsters are able to carefully target users with very convincing replicas that misdirect their unsuspecting targets into entering erroneous account info.
Property purchases can be a particularly devastating example of APP fraud. Both individuals and business can fall from the intercepted messages between buyers, sellers, agents and solicitors. By jumping into an emails chain, just at the right moment, criminals can use look-alike, or even compromised email addresses to request funds be misdirected.
How CoF Works
Confirmation of Payee essentially does what it says on the tin. To make a transfer, banks currently require users to input three basic information fields: name, account number and sort code. The way payments are processed means both the account number and sort code are verified, though the name provided by the payer does not have to match that of the payee for the payment to be made.
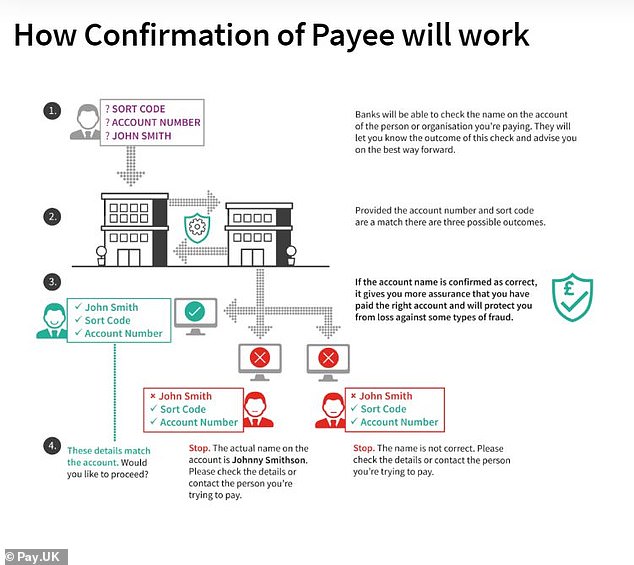
For many, this is an issue which cannot be solved fast enough, and confirmation of payee will certainly help those wishing to make transfers to avoid sending payments to fraudsters’ accounts. Though this is undoubtedly a step in the right direction, CoP does not come without its downsides.
In their research in the matter Pay.UK have pointed out that for joint accounts, those with tricky or unusual names, certain ‘translated’ names and common misspellings, there may be some requirement for banks to inform users of a payee ‘close-match’ rather than disallowing the payment completely.
As users and bank customers await these changes to be implemented, we must all be aware that there are still currently (and always will be) methods and avenues by which scammers will attempts to take advantage of both our digital infrastructure and our human fallibility. CoP will undoubtedly help to reduce APP scams, though how much remains to be seen.
Authorised/Unauthorised Push Payments
Unlike Authorised Push Payments, customers are in fact currently protected from the Unauthorised variety. As opposed to customers being tricked into making a transfer, APP fraud is when a transfer is made by someone other than the account holder.
This can happen because of account compromise or numerous other nefarious methods, and according to research cited by UK Finance, 98% of unauthorised fraud cases result in full refunds to customers. A protection that victims of APP fraud are far from having.
How can I protect myself from APP fraud?
Don’t Hand Over Account Details – Be especially wary if any organisation (even your bank) asks for sensitive information. Attacks designed to trick you into parting with this info can come in the form of emails, phone calls and SMS messages. Even if you believe a caller to be genuine, phone numbers can be ‘spoofed’ and it’s always better to verify a number and call back.
Verify Details – In both your personal and professional life, you should always take the time to verify account information included within an invoice or request, especially if the message conveys urgency. If you receive a transfer request in email form, pick up the phone and check with the sender that the message came from them and that the details are correct. Once the transfer is complete, it can be impossible to retrieve funds.
Take Your Time – As mentioned above, fraudsters will often try and scare or hurry users into making a transfer. It’s very infrequent that reputable organisations will demand funds be transferred immediately.
Be Willing to Say No – Listening to your instincts. If something doesn’t feel right about an exchange or conversation, be happy to say no. Again, reputable and trustworthy parties should be appreciative of reasonable scepticism and not try and pressure you into handing off your information or funds.
Security Awareness for your Organisation
Enjoyed our blog? Learn more about how Hut Six can help improve you security awareness with training and simulated phishing. Start a free trial now, or book a meeting with one of our experts.
Featured
Spear Phishing Series Part 2: How to Spot a Spear-Phishing Email
Spear phishing is one of the most effective ways of gaining sensitive information. These highly targeted attacks use your personal information against you.
Human Rights and the Growing Surveillance Economy
Human Rights and the Growing Surveillance Economy: Surveillance capitalism can mean your information being sold to the highest bidder. Blog by Hut Six
Attention: HP's Self-Destructing Firmware
HP firmware issue: The technology manufacturer Hewlett Packard has announced a firmware issue that could affect thousands of enterprise users. SSDs sold by the company are at risk.
Spear Phishing Series part 1: How a Spear-Phishing Email is Created
How is a spear-phishing email created? Cybersecurity blog from information security awareness training provider Hut Six Security.
Information Security vs Cyber Security: What’s the Difference?
How is it that information security and cyber security differ, and why is it that people frequently use these terms interchangeably?
The Cost of Poor Information Security
Facebook ICO fine and the cost of poor information security. Blog from information security awareness training provider Hut Six Security.
Cyber Security Awareness Month: Once a year, all year.
Cyber security Awareness month creates a problem in focus for companies. Blog from information security awareness training provider Hut Six Security.
New from Hut Six: Scenario-based branching Tutorials
Cybersecurity training modules that give the user the ability to test their skills. Blog from information security awareness training provider Hut Six.
Micro-businesses are underestimating social engineering
Are micro businesses underestimating social engineering? Blog from information security awareness training provider Hut Six Security.
General Data Protection Regulation
What does General Data Protection Regulation mean for my business? GDPR Blog from information security awareness training provider Hut Six Security.










