Malicious Insider Threats
Within the field of information security there are a litany of threats which organisations are forced to deal with. From spear phishing attacks to compliance issues, social engineering to data privacy, though, perhaps no other security issue is quite as troubling or as complex as the problem of insider threats.
Whether these incidents are due to negligence, ignorance, or malice, insider threats can have massive implications not only on the security of an organisation, but also their finances and reputation.
According to leading research, the average annual cost to organisations dealing with insider security incidents has grown over 80% in the last 4 years, rising from $8.3 million in 2018 to over $15.3 million in 2022.
With the frequency of these incidents increasing as well, much of the attention is often given to the negligent variety of insider threat. While much can be said about accidental human error, information security training, and various other mitigation techniques, in this article we are going to be taking a much-needed closer look at the malicious insider.
We will be exploring the motivations of the malicious insider, including some of the psychological traits associated with this behaviour, as well as exploring the latest findings regarding non-technological detection and prevention methods.
Insider Threat Statistics
27% of data breach incidents were caused by human factors or negligence.
The average time to contain an insider threat incident is 85 days.
Incidents that took more than 90 days to contain cost organisations an average of $17.19 million on an annualised basis.
12.1% of incidents (2017-2018) reported to the UK's Information Commissioner's Officer (ICO) were determined to be deliberate malicious actions.
Average annual cost now $15.3 million.
Only 11% of organizations consider their monitoring, detecting, and response to insider threats extremely effective.
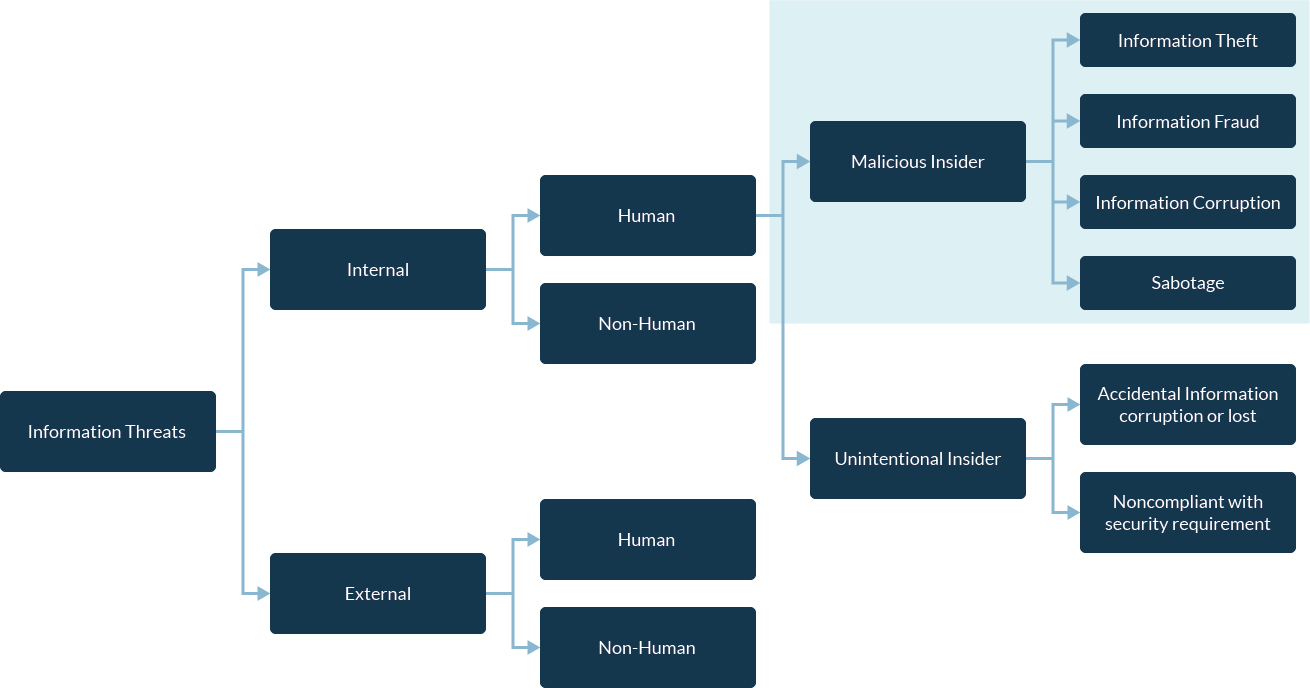
What is an Insider Threat?
Insiders can come in many forms, though generally speaking, when we talk in the context of information security, we think of an individual with whom an organisation has a trusted relationship.
This is most commonly an employee (or former employee), though could also be a contractor, vendor, or other associated party who has access or knowledge to sensitive information that an organisation seeks to protect.
The threat element of insider threat, as previously noted, does not necessarily need to be malicious, that is intentional, but their actions or behaviour does threaten the security of an organisation in some respect.
Breaking this down further, there are three generally accepted types of insider threat worth defining:
The Compromised insider: An insider whose account credentials have been harvested or stolen, and without malice or intention, inadvertently allows an attacker to gain access to sensitive information. For example, the unknowing victim of a spear phishing attack.
The Careless insider: Those individuals who make the most common or avoidable of mistakes and do not pay significant enough attention to the security policies of the organisation. For example, an employee who fails to properly secure confidential information.
The Malicious insider. The category of our focus, the malicious insider (sometimes known as an 'intentional insider') is an individual who purposefully abuses legitimate access to steal information for financial or personal gain. For example, the employee who seeks to sell intellectual property to a competitor.
Motivations of Malicious Insiders
As with all types of criminal activity, the motivations of malicious insiders vary, and in some cases, are not always clear. That being said, it probably doesn't come as a surprise that the vast majority of malicious insider attacks are believed to be financially motivated (most research suggesting around 80%).
Interestingly, according to a study conducted by the National Threat Assessment Center of the United States Secret Service and the CERT Coordination Center, 27% of the malicious attackers studied were going through financial difficulties at the time of their attack.
While the majority of insider attacks are motivated by monetary gain, there are other incentives, including revenge, vengeance, or dissatisfaction, with some individuals even citing the desire for respect as a motivating factor.
Additionally, there are also those rare incidents of politically motivated insider attack. Perhaps the most infamous case of which is that of Chelsea Manning, the former US army intelligence analyst who was, in 2013, convicted by court-martial for violating the Espionage Act following the disclosure of almost a quarter of a million classified and sensitive military and diplomatic documents to WikiLeaks.
Though these motivating factors are useful in gathering insight into this security issue, before we seek to extrapolate any specific insight from these observations, it is first worth delving a little deeper into the research regarding the profile of an insider threat.
Predicting Insider Threats
Backgrounds
Drawing from research conducted by, amongst others, the United States Secret Service, there are some interesting findings regarding the backgrounds and profiles of insider threats.
Firstly, only 23% of malicious insiders were found to have been from technical positions, with the typical insider working with a normal or average level of technical expertise; and while it may be reasonable to theorise that more technically capable individuals pose a potentially higher risk, evidence to support this notion is unavailable.
Interestingly, most of those examined also had between 2 to 5 years of working history within the organisations they targeted, and were not, as you'd may expect, particularly quick to move between jobs.
Additionally, in another piece of research, it was revealed that 92% of all studied insider attacks followed a negative-work-related event "such as termination, dispute with a current or former employer, demotion, or transfer."
Threat Indicators
Based on the case studies of documented insider threat incidents, academics and researchers have put together various models for identifying actors. One of the most commonly cited is that of Greitzer et al..
Consisting of 12 psychosocial indicators, this model seeks to determine whether a party is a potential malicious insider threat based on individual scores. These indicators (or risk factors) are as follows:
- disgruntlement,
- not accepting feedback,
- anger management issues,
- disengagement,
- disregard for authority,
- performance issues,
- stress,
- confrontational behaviour,
- personal issues,
- self-centredness,
- lack of dependability, and
- absenteeism.
With observation-based data points drawing from human resources, performance reviews, and security behaviour, researchers believe these indicators contribute differentially to the level of psychosocial risk, with disgruntlement, difficulty accepting feedback, anger management issues, disengagement, and disregard for authority having higher weights than other indicators.
While it is worth pointing out (as one of the main authors behind this work states) "the relationship between behavioural factors and insider threat risk remains largely untested", considered alongside the broader scope of research, it is worthwhile for security professionals to keep these factors in mind as they may offer useful insight into identifying and mitigating potential threats.
Mental Health & Wellbeing
One of the more challenging findings that repeatedly appears within many areas of security literature, is that of the mental health aspect.
Before we delve into this issue, it's relevant to note that much of the research into insider threats is relatively imprecise.
Given that many organisations understandably do not wish to share detailed accounts of internal security incidents (or sensitive employee data), and that much of the research is based on media coverage and other non-professional psychological assessments, the observations here should not be treated as definitive, but rather seen as a potential element of a wide variety of indicators.
From paranoia to narcissistic personality disorder, to substance abuse and anger management problems, there are various mental health issues which researchers have suggested may in some way act as indicators for potential threat actors.
To what degree these mental health conditions are linked to insider threat behaviour, is something of an unknown, with some research even suggesting that these characteristics are perhaps no more prevalent amongst insider threats than the general population.
Despite this, the choice to include this factor within this article is to highlight the importance of organisations accounting for the general wellbeing of their employees.
According to research conducted by the World Health Organisation (WHO), it is estimated that globally 12 billion working days are lost every year to depression and anxiety alone, yet by providing a healthy and positive work environment, organisations can reduce workplace conflicts, improve staff retention, and minimise a variety of negative behaviours.
"Employee mental health is critical. Besides destroying lives, suffering can destroy the human spirit that drives innovation, economic energy, and eventually, good jobs."
Jim Clifton, Gallup chairman and CEO, State of the Global Workforce: 2021 Report
While an employer is not ultimately responsible, or in many cases even privy to the mental health issues of their employees, it is not unreasonable to posit that by seeking to optimise employee wellbeing, an organisation can additionally minimise potential security risks; fulfilling both business and moral goals in a mutually beneficial manner.
Mitigating Insider Threats
So far, we have looked at some of the factors associated with insider threats and potential identification indicators, but to contextualise this information, we must also examine practical steps for insider threat detection.
Though there are many effective and valuable technological tools available, from zero-trust systems and network monitoring, to machine-learning-based behavioural analytics and many more, below are recommendations specific to non-digital insider threat detection.
Employee Monitoring & Assessments
Touched upon previously, there are many factors which are potentially useful in identifying threats, and while the methods and extent of employee scrutiny will vary massively depending on the level of security necessary for a role, there are some common lessons to be learnt.
At the highest level, organisations should be looking for certain key indicators in terms of employee behaviour. Managers and human resources alike should be particularly vigilant of the following traits:
Anger management issues.
Difficulty accepting feedback.
Disengagement.
Disregard for authority.
A history of criminal activity.
Although there is no exact profile for an insider threat (nor the exhibiting of these behaviours evidence of malicious activity), by monitoring these various indicators, potential risk-associated individuals could be identified, with further data points (such as a significant negative workplace incident) being leveraged to further pinpoint possible threats.
Awareness Training & Reporting
As several pieces of research have found, not only do attackers often plan their crime, but also, in many cases a third-party knew of the forthcoming attack.
Being frequently detected and reported by co-workers, we could reasonably draw the conclusion that by implementing both effective awareness training and a robust reporting system, organisations could greatly improve their likelihood of successfully detecting insider threats (potentially even prior to an attack being executed).
Educating employees about potential threat indicators and the various factors which play into this challenging information security issue is essential; with experts lamenting the need for organisation to encourage employee engagement in this security domain.
Responding to an Insider Threat
Should you or your organisation identify an insider threat, your response is dependent on several factors, including:
Is there threat potential, or has an incident actually occurred?
Is any action unintentional or malicious?
Who or what is affected by the incident? (i.e., personal data, IP, stakeholders)
Should an individual be identified about whom there is a concern, your response may range from supplementary training (knowledge or skills-based concerns) to increased monitoring of network activity (potential malicious insiders), or the launching of an internal investigation.
If an incident has occurred, the nature of the incident will play a large role in guiding your response. For instance, should personal data be involved, then you may have a legal obligation to report the incident to the UK's Information Commissioner's Office (ICO).
In instances when an intentional threat incident has occurred, this would (depending on employment contracts) likely constitute negligence and thus be grounds for dismissal; and you may even be advised to report more extreme (most likely intentional) incidents to law enforcement.
Noted at the start of this article, insider threats are a particularly challenging area of information security. With many malicious insiders taking steps to cover their actions, a lack of a generalised profile, as well as the need for further robust research into behavioural factors, security advice can often be somewhat vague.
Although there is no silver bullet, and identifying mitigating insider threats will always be an uphill battle, hopefully, with this overview of research we have given the reader some points to consider, as well as adding to an overall understanding of this pressing information security threat.
Security Awareness for your Organisation
Enjoyed our blog? Learn more about how Hut Six can help improve you security awareness with training and simulated phishing. Start a free trial now, or book a meeting with one of our experts.
Featured
5 Biggest Breaches of 2022 (So Far)
Five of the biggest and most significant data breaches, hacks, and information security attacks of 2022 (so far).
Auditing for GDPR Compliance
Questions to consider when auditing your business or SME for General Data Protection Regulation (GDPR) compliance.
Improving Employee Cyber Security
With human error responsible for many breaches and attacks, we offer some helpful areas for improving employee security compliance.
5 Cyber Tips for your Business
Essential cyber tips for helping your business or SME improve information and cyber security.
The Benefits Of Maintaining Compliance For Your Business
By maintaining compliance for your business you can ensure operational efficiency, reduce financial risk, enhance public trust, engage your employees and realise your mission.
Top 5 Phishing Trends in 2022
Insights, trends, and statistics from the world of phishing in 2022.
10 Steps to Cyber Security
The main concepts of the Nation Cyber Security Centre's '10 Steps to Cyber Security' guidance.
Cyber Awareness Part II: The Psychology of Behaviour Change
Part two in our blog series examining how the psychology of behaviour change will help us deliver effective awareness campaigns.
5 Anti-Phishing Insights Every CISO Should Know
Based the latest scientific research, tips to reduce human error and protect businesses against phishing attacks.
Cyber Awareness Part I: The Psychology of Behaviour Change
Cyber awareness helps reduce human error and insecure behaviours. Examining how the psychology of behaviour change will help us deliver effective awareness campaigns.










